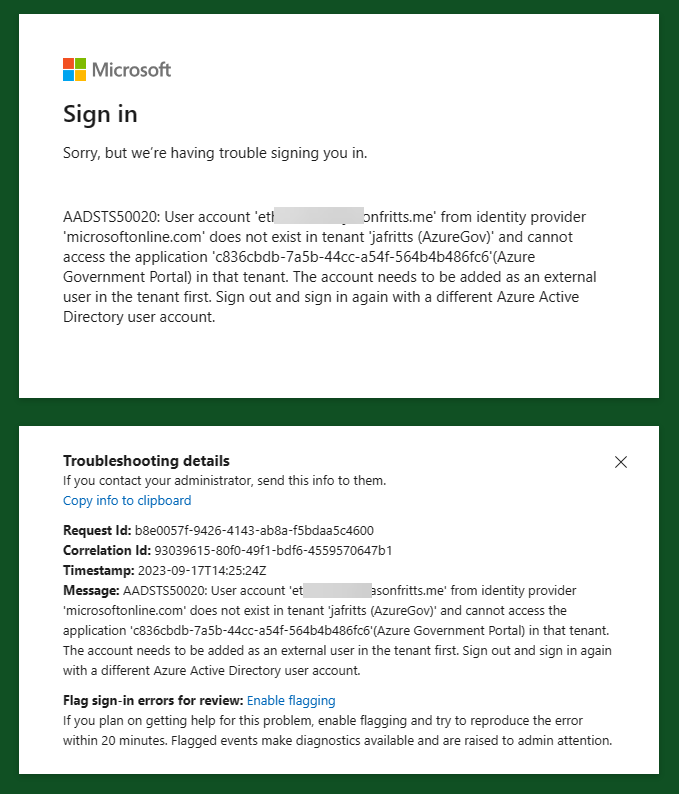
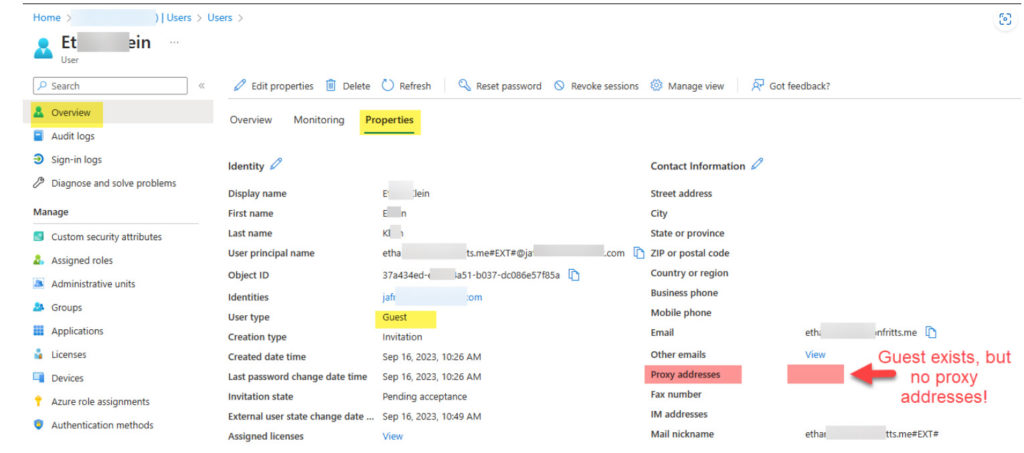
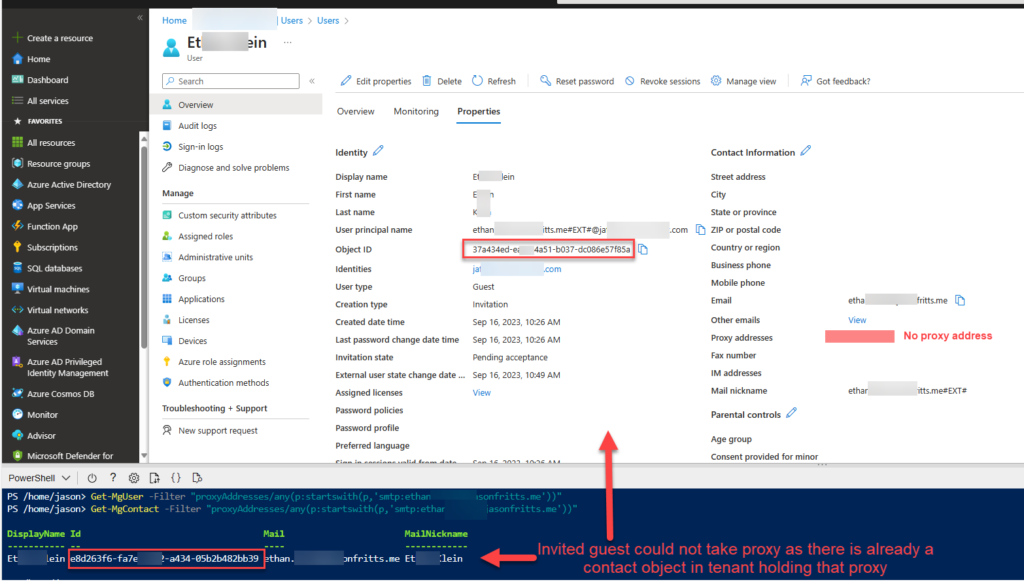
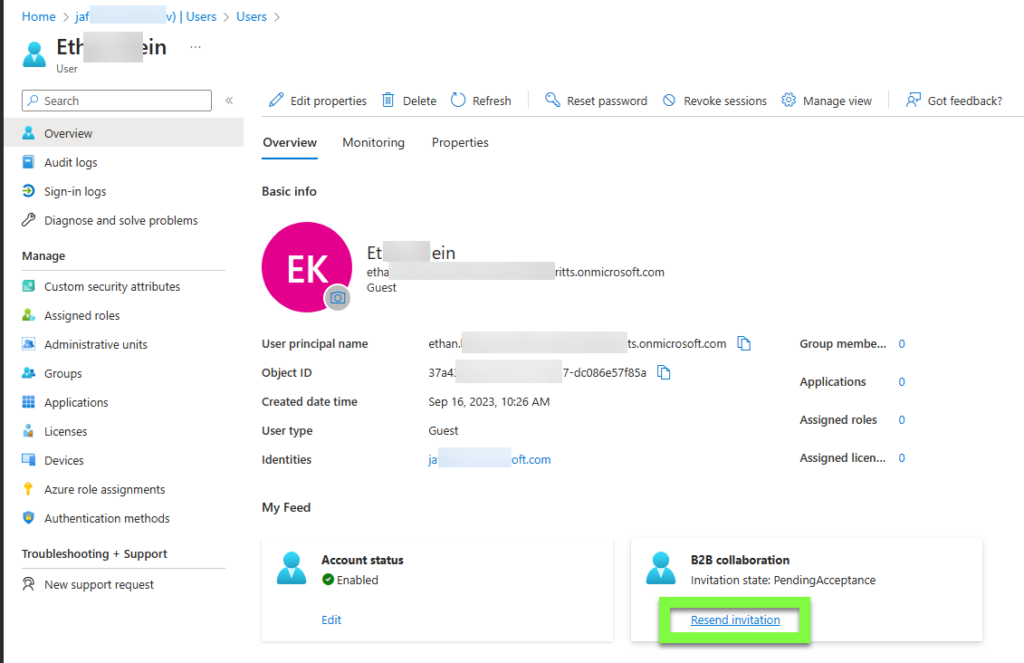
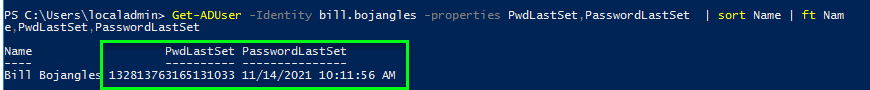
The following steps can be used to easily export all Azure role assignments from a tenant to a CSV including management group scope, all subscriptions in tenant, and all children scopes like resource groups and resource assignments. This process utilizes the Azure Resource Graph Explorer available in the Azure Portal and the new AuthorizationResoruces table avaiable in Azure Resource Graph
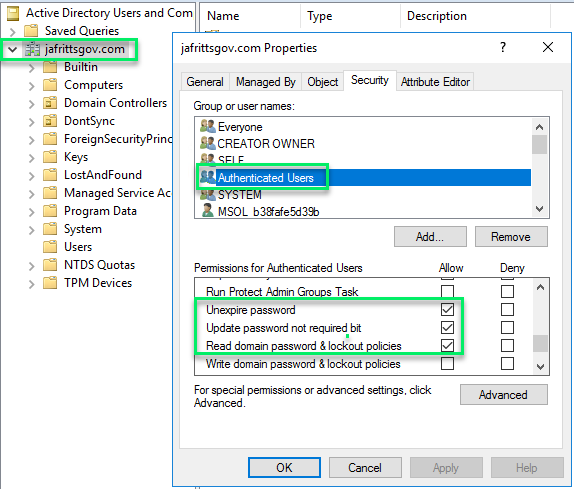
- Verify you are Global Admin and have followed Elevate access for a Global Administrator so that you have User Access Administrator role at “/” root scope of tenant. Without following this step you will not have the ability to query role assignments outside of the scope\subscription you have access to.
- Log out and Log in to https://portal.azure.com if you recently elevated yourself to “/” root scope access.
- You can confirm you have permissions at “/” root scope by browsing to the Azure Portal’s Management Groups blade -> Tenant Root Group -> Access control (IAM) -> Role assignments and confirming you see you have at least User Access Administrator role at the Root scope listed.
NOTE: You can still run the query without root scope permissions, but you will only find role assignments for the subscriptions you have read access to. - From https://portal.azure.com, browse or search to the “Azure Resource Graph Explorer” (https://portal.azure.com/#view/HubsExtension/ArgQueryBlade)
- Change your authorization scope to “At, above and below”
- Run the following query to list all role assignments in tenant:
authorizationresources
| where type == "microsoft.authorization/roleassignments"
| extend scope = tostring(properties['scope'])
| extend principalType = tostring(properties['principalType'])
| extend principalId = tostring(properties['principalId'])
| extend roleDefinitionId = tolower(tostring(properties['roleDefinitionId']))
| mv-expand createdOn = parse_json(properties).createdOn
| mv-expand updatedOn = parse_json(properties).updatedOn
| join kind=inner (
authorizationresources
| where type =~ 'microsoft.authorization/roledefinitions'
| extend id = tolower(id)
) on $left.roleDefinitionId == $right.id
| mv-expand roleName = parse_json(properties1).roleName
| project createdOn, updatedOn, principalId, principalType, scope, roleName, roleDefinitionId
- Export via Download as CSV button
- You can also customize your query to only return role assignments matching a particular role definition ID or principal ID etc. like the following query which will only return role assignments for a custom role definition ID
authorizationresources
| where type == "microsoft.authorization/roleassignments"
| extend scope = tostring(properties['scope'])
| extend principalType = tostring(properties['principalType'])
| extend principalId = tostring(properties['principalId'])
| extend roleDefinitionId = tolower(tostring(properties['roleDefinitionId']))
| mv-expand createdOn = parse_json(properties).createdOn
| mv-expand updatedOn = parse_json(properties).updatedOn
| join kind=inner (
authorizationresources
| where type =~ 'microsoft.authorization/roledefinitions'
| extend id = tolower(id)
) on $left.roleDefinitionId == $right.id
| mv-expand roleName = parse_json(properties1).roleName
| where roleDefinitionId contains "8de27061-dc9b-4500-9326-0454510bf635"
| project createdOn, updatedOn, principalId, principalType, scope, roleName, roleDefinitionIdYou can find other queries ane examples at the following links:
Table announcement:
https://techcommunity.microsoft.com/t5/azure-governance-and-management/announcing-authorizationresources-in-azure-resource-graph/ba-p/3813912
Using table to find classic co-administrators:
https://learn.microsoft.com/en-us/azure/role-based-access-control/classic-administrators?branch=pr-en-us-263308&tabs=azure-resource-graph
Hope these examples are helpful to someone!