The following are my notes for setting up SAML/WS-Fed identity provider (IdP) federation for Guest users (formerly known as Azure AD B2B Direct Federation) with a GSuite domain. The official documentation can be referenced at https://docs.microsoft.com/en-us/azure/active-directory/b2b/direct-federation.
UPDATE
A couple key points to highlight before you begin configuring SAML/WS-Fed identity provider (IdP) federation for Guest users , please review the different federation scenarios on Azure AD and GSuite Federation Scenario Notes before beginning to verify this configuration is right for your scenario.
- This feature has been renamed to SAML/WS-Fed identity provider (IdP) federation for Guest users.
- This guide is for configuring a federation relationship with a GSuite domain so that you can invite B2B Guest users to your AAD tenant when those users do not have their own Azure AD work\school accounts. It is NOT intended for configuring a SAML federated domain in your Azure AD tenant for SAML Authentication of your own GSuite users. For that process review Scenario 1 in Azure AD and GSuite Federation Scenario Notes
- Once the B2B External Identity SAML federation has been configured, you MUST invite the GSuite Users to your tenant via a B2B Guest Invitation by folllowing Add guest users to the directory Once invited, the guest users MUST visit one of the supported tenanted URLs such as https://portal.azure.com/resourcetenant.onmicrosoft.com as described in supported Sign-in endpoints for SAML/WS-Fed docs . If they try to sign in via any other method (for example IDP initiated sign in) they will receive an error of the form ‘The requested federation realm object ‘https://accounts.google.com/o/saml2?idpid=xxxxxx’ does not exist.’ , meaning they tried to sign in to a common endpoint like https://portal.azure.com or https://myapps.microsoft.com.
- Note that if you only want to invite Gmail.com users you can use Google Federation steps instead https://docs.microsoft.com/en-us/azure/active-directory/b2b/google-federation
Steps to configure AAD B2B Direct Federation with GSuite Domain
- Login to https://admin.google.com -> Security -> Authentication -> SSO with SAML Applications -> Download Metadata file

- Choose Download Metadata, and save the returned GoogleIDPMetadata.xml locally
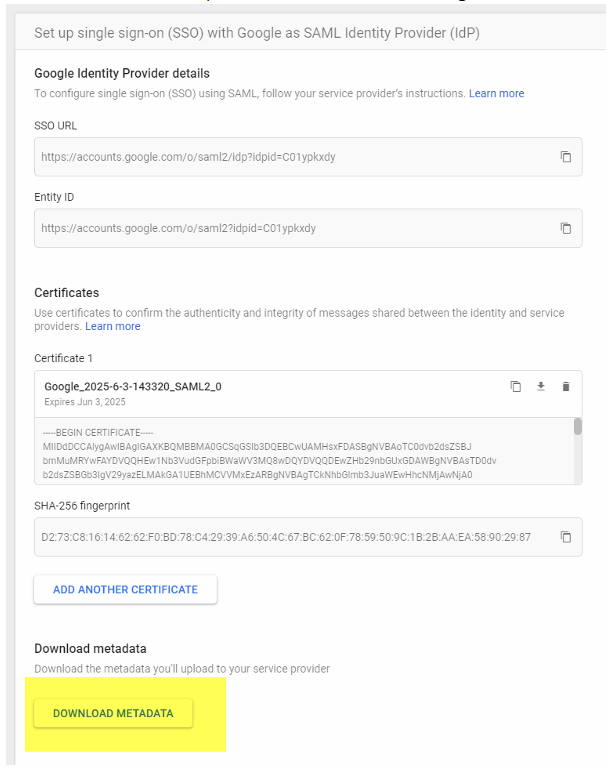
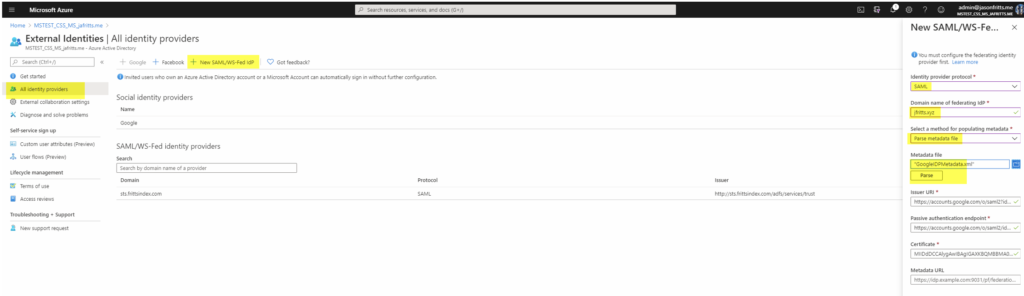
- Browse to https://portal.azure.com -> Azure AD -> External Identities -> All identity providers -> New SAML/WS-Fed IdP . Choose protocol = SAML, domain name = gSuite domain name, method = parse metadata file. Browse to your GoogleIDPMetadata.xml file and hit parse, then save:
- From https://support.google.com/a/answer/6363817?hl=en follow Step 3. “Set up Google as a SAML identity provider (IdP)” and Browse to https://admin.google.com -> Apps -> SAML Apps -> New App
- Filter existing apps by “Microsoft Office 365” and add the app
- Download Metadata locally to .XML file
- Save
- Browse back to apps and choose “Microsoft Office 365”
- Edit Attribute Mapping to be as follows
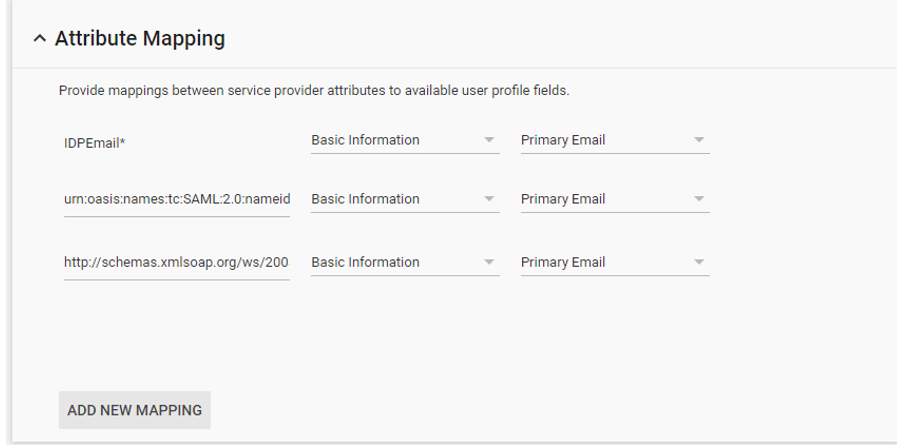
| IDPEmail* | Basic Information | Primary Email |
| urn:oasis:names:tc:SAML:2.0:nameid-format:persistent | Basic Information | Primary Email |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress | Basic Information | Primary Email |
- From https://support.google.com/a/answer/6363817?hl=en follow Step 5. “Enable the Office 365 app” and Choose Edit Service -> Service Status -> ON for everyone
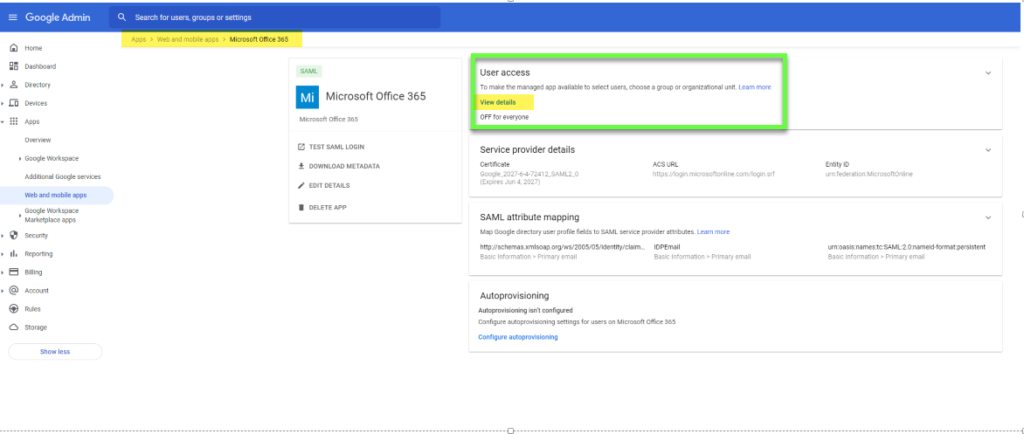
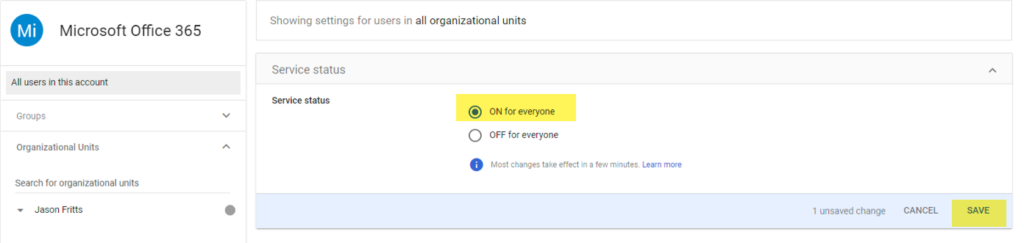
- Lastly Invite the Guest GSuite domain User from Azure AD
- Now From Azure AD portal -> Invite New User -> Invite a user from G Suite domain
- G Suite user gets invite email, and clicks redemption link and signs in with G Suite credentials to redeem invite successfully
Finally, if needed you can manually configure GSuite Direct Federation using Azure AD Preview PowerShell module and example script below (note your GSuite metadata will be different)
Connect-AzureAD $federationSettings = New-Object Microsoft.Open.AzureAD.Model.DomainFederationSettings $federationSettings.PassiveLogOnUri ="https://accounts.google.com/o/saml2/idp?idpid=C01ypkxdy" $federationSettings.ActiveLogOnUri = "https://accounts.google.com/o/saml2/idp?idpid=C01ypkxdy" $federationSettings.LogOffUri = "https://accounts.google.com/o/saml2/idp?idpid=C01ypkxdy" $federationSettings.IssuerUri = "https://accounts.google.com/o/saml2?idpid=C01ypkxdy" $federationSettings.SigningCertificate= "MIIDdDCC_EXAMPLECERT_lMlRYzq4" $federationSettings.PreferredAuthenticationProtocol="Samlp" $domainName = "jfritts.xyz" New-AzureADExternalDomainFederation -ExternalDomainName $domainName -FederationSettings $federationSettings