You are here because you have invited an external user to your Entra (formerly Azure AD) tenant via B2B Guest invitations and when signing in to your tenant the external user receives an error such as the following:
“User account ‘{_email}’ from identity provider ‘{idp}’ does not exist in tenant ‘{tenant}’ and cannot access the application ‘{appId}'({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.”
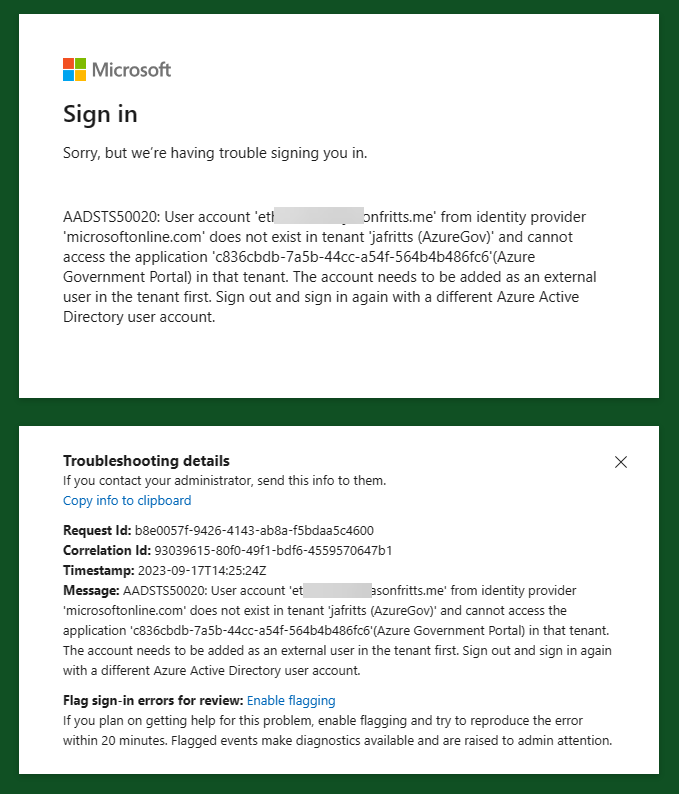
This error comes in various forms of error codes such as any of the following:
AADSTS16003
AADSTS50020
AADSTS500211
AADSTS50034
AADSTS50177
AADSTS50178
AADSTS51004
AADSTS90072
However, they all mean essentially the same thing. The user who has signed into their own tenant (identified by the “from identity provider X” section of the error) succesfully, is trying to access a resource tenant (identified by the “does not exist in tenant Y” section of the error) and AAD cannot find any Guest user object in tenant Y with a matching proxyAddress.
Troubleshooting Steps
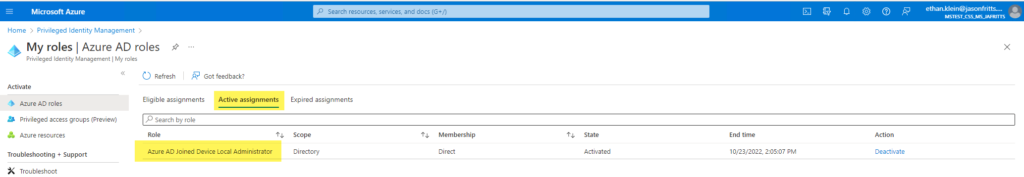
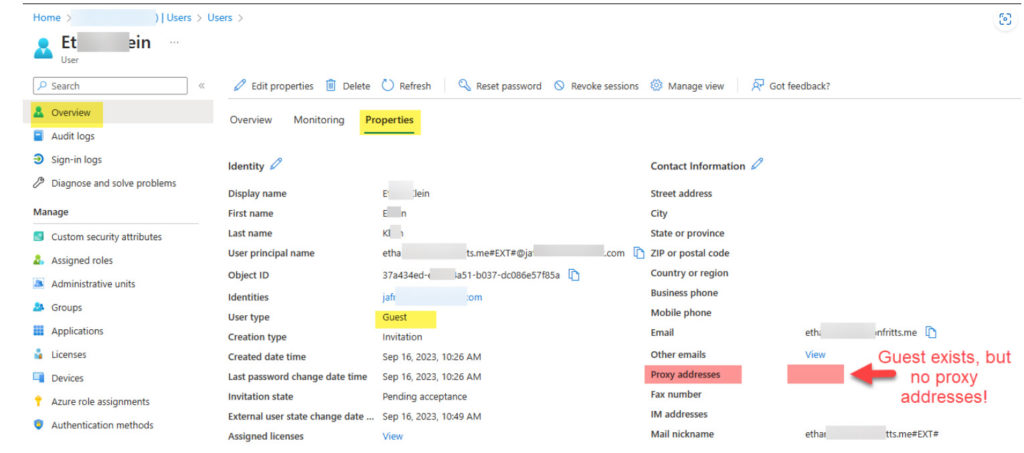
- Verify that a user object exists in the resource tenant matching the user name from the error message and note whether Invitation State =
Pending AcceptanceorAccepted. If invite is already Accepted, go to step 8. - Verify that on the Guest user object found in the resource tenant, that the username from the error message exists as a ProxyAddress
smtp:user@contoso.com - If no user is found in resource tenant, then the user must be invited first
- If a user is found, but they have no ProxyAddress attribute matching the invited guest, then when the user was invited there may have been a duplicate proxyAddress error. See the following public docs on scenario.
- To locate the duplicate proxyAddress in the directory, the admin can query the tenant using Graph Powershell Module
# Define the proxyAddress to search for
$proxyAddress = "user@contoso.com"
# Get all users and contacts from the Microsoft Graph API
Get-MgUser -Filter "proxyAddresses/any(p:startswith(p,`'smtp:$proxyAddress`'))"
Get-MgContact -Filter "proxyAddresses/any(p:startswith(p,`'smtp:$proxyAddress`'))"
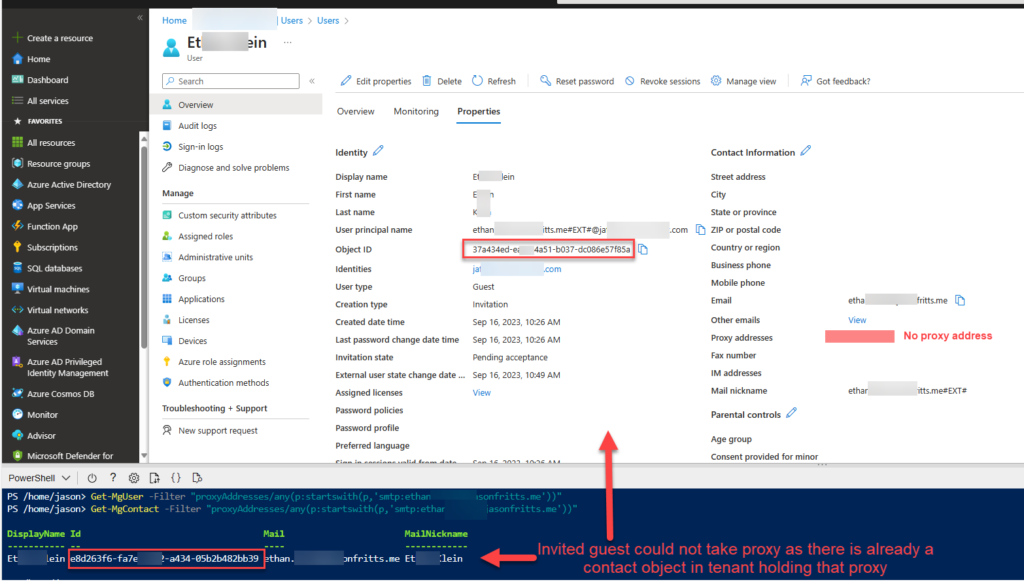
Example of how to use Graph Powershell to find User or Contact object containing proxyAddress
- Once the object holding the user’s proxyAddress is located, the administrator can delete this user and then reinvite the Guest user to populate the proxyAddress
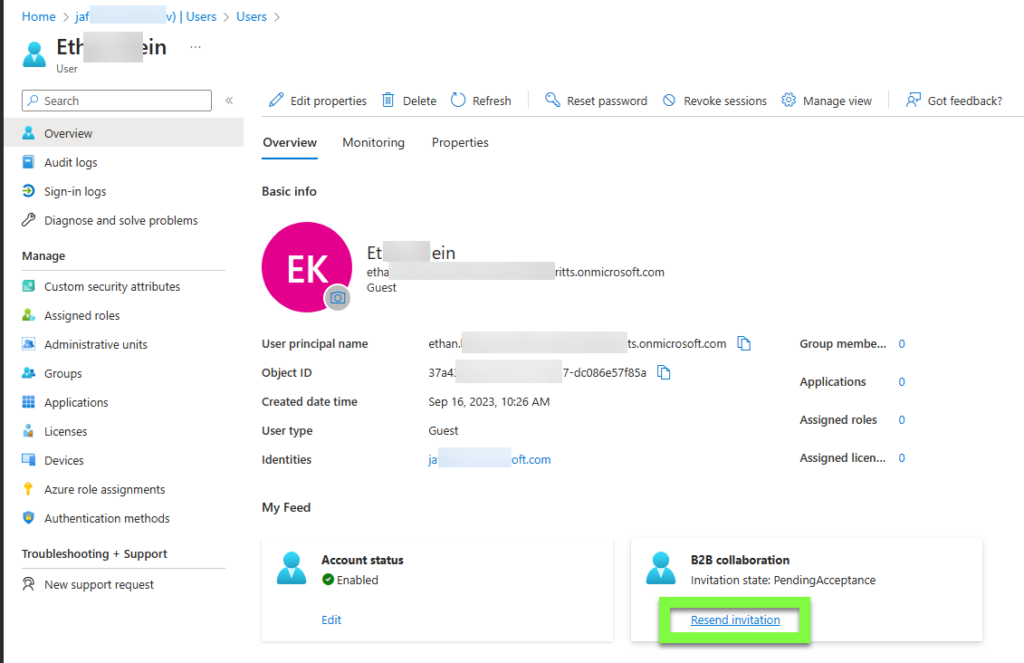
Using resend invite to populate ProxyAddress value \ Send direct redemption link
- Alternatively, the administrator can send the user a direct redemption link via the Resend invitation or asking user to click the Accept invitation link found in invitation email. These links (starting with
https://login.microsoftonline.com/redeem) are direct invite redemption links and will not require lookup of proxyAddress in resource tenant.
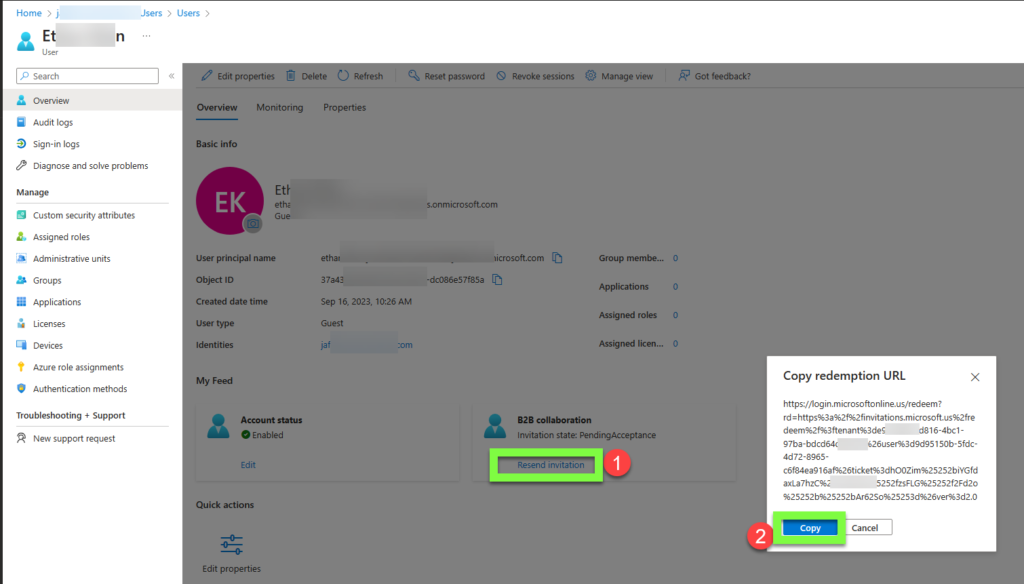

- If the guest user does exist AND has a matching proxyAddress but the error still persists, then the guest invitation may have already been accepted (Invite state =
Accepted) by a user whose home account PUID \ ObjectID has since changed. Usually the user’s home object ID has changed after being recreated since originally accepting invite.
In this scenario, resource tenant admin will need to reset redemption state on the guest user so the external user can accept the invite again. See Check whether guest alternative security id differs from the home tenants net ID
PS. You can find some additional troubleshooting steps in the public doc for Error AADSTS50020 – User account from identity provider does not exist in tenant article
Thanks for reading and hope it helps someone troubleshoot their B2B sign in failure!